Vulnerability Management
Detect, Prioritize, and Remediate Critical Vulnerabilities
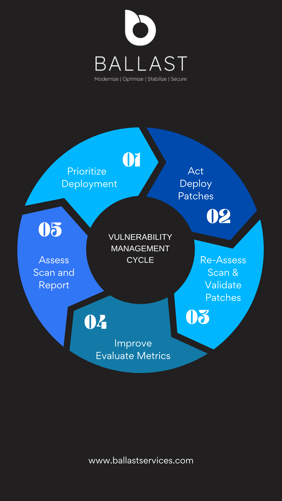 Vulnerabilities are weaknesses in software, systems, or infrastructure that can be exploited by threat actors to gain unauthorized access, steal sensitive data, or cause damage to your technology investment. In today's technology-reliant world, vulnerabilities are an ever-present threat that can have far-reaching consequences for your organization. Exploiting known and unpatched vulnerabilities is a common tactic for advanced threat actors who understand organizations often struggle to identify and implement critical patches.
Vulnerabilities are weaknesses in software, systems, or infrastructure that can be exploited by threat actors to gain unauthorized access, steal sensitive data, or cause damage to your technology investment. In today's technology-reliant world, vulnerabilities are an ever-present threat that can have far-reaching consequences for your organization. Exploiting known and unpatched vulnerabilities is a common tactic for advanced threat actors who understand organizations often struggle to identify and implement critical patches.
Ballast’s best practice-based vulnerability management service proactively identifies and addresses security risks, minimizes the impact of successful attacks, and meets regulatory and compliance requirements. Vulnerability management is an essential component of your organization's successful security program. By identifying, assessing, and mitigating security threats, we will proactively reduce the risk of successful attacks and improve the security of your systems and data.
Vulnerability management is an essential component of your organization's successful security program. By identifying, assessing, and mitigating security threats, we will proactively reduce the risk of successful attacks and improve the security of your systems and data.
Service Benefits
Proactive Real-time scanning
Of Your Web Applications and IT Infrastructure
Advanced risk reporting
Identifies and Prioritizes Critical Vulnerability and Exposure (CVE) in Your Environment
Industry-leading threat intelligence
Keeps Up With the Ever Changing Vulnerabilities Attackers Use to Exploit Your Company
Know your vulnerabilities
Plan, Assess, and Execute Patch Management at Speed
Understand What's In Your Network
Via Advanced Discovery Scans and Inventory Asset Reports
Meet Governance, Risk, and Compliance (GRC) requirements
For Your Business with Intelligent Audit Reports

Service Benefits
Proactive Real-time scanning
Of Your Web Applications and IT Infrastructure
Advanced risk reporting
Identifies and Prioritizes Critical Vulnerability and Exposure (CVE) in Your Environment
Industry-leading threat intelligence
Keeps Up With the Ever Changing Vulnerabilities Attackers Use to Exploit Your Company
Know your vulnerabilities
Plan, Assess, and Execute Patch Management at Speed
Understand What's In Your Network
Via Advanced Discovery Scans and Inventory Asset Reports
Meet Governance, Risk, and Compliance (GRC) requirements
For Your Business with Intelligent Audit Reports






Understand which of your assets need to be protected and where they are located.
Our platform automatically tests your systems and applications for known vulnerabilities and generates real-time alerts when critical vulnerabilities are discovered.
After vulnerabilities have been identified, our reports provide context-based results that prioritize patches and potential workarounds to mitigate risk.
Our team will implement measures to mitigate the discovered risks via patching, implementing new security controls, or increasing awareness and training for employees through our comprehensive suite of managed solutions.
Our Team Is Your Team
Our SOC and cybersecurity engineers become part of your team. We provide 24x7 cybersecurity services for your business which monitor and alert on multiple technologies and equipment manufacturers. We do the heavy lifting by monitoring and reacting to security alerts and events using the MITRE ATT&CK Framework, so your team can focus on internal projects and initiatives that move your business forward.
Security Focused Managed Services
Everything we do is focused on modernizing, optimizing, stabilizing, and securing your technology environment. Our focus is not just day-to-day operations; we focus on continuous service improvements, capacity planning, change management, and the security of your systems.
Our Methodology
Our ITIL based methodology includes a mature 5 phase service transition process, refined service operations procedures, and a consistent rigor focused on continual service improvement. Service management is critical to our delivery to you, and we constantly share key performance indicator metrics and make recommendations to ensure a strong partnership with your business.
Ballast Services Named to MSSP Alert’s 2023 List of Top 250 MSSPs
Ballast Services ranks among the Top 250 MSSPs for 2023, according to MSSP Alert, a CyberRisk Alliance resource.
Why You Need a Patch Management Program ASAP
Along with phishing, unpatched vulnerabilities are the most common way cybercriminals gain access to internal systems to deploy malware and steal data. Over 25,000 software vulnerabilities were discovered in 2022 alone.
Bracing for Impact: Navigating Disaster Recovery with Ballast Services
Disaster does not discriminate based on geography or industry – it can strike any organization, at any time, in any form. Whether it’s a hurricane, tornado, Flooding, a successful ransomware attack, supply chain disruption, or extended power outage, businesses need to be prepared to ensure continuous operations even when disaster strikes.
Ballast Services Named to MSSP Alert’s 2023 List of Top 250 MSSPs
Ballast Services ranks among the Top 250 MSSPs for 2023, according to MSSP Alert, a CyberRisk Alliance resource.
Why You Need a Patch Management Program ASAP
Along with phishing, unpatched vulnerabilities are the most common way cybercriminals gain access to internal systems to deploy malware and steal data. Over 25,000 software vulnerabilities were discovered in 2022 alone.
Bracing for Impact: Navigating Disaster Recovery with Ballast Services
Disaster does not discriminate based on geography or industry – it can strike any organization, at any time, in any form. Whether it’s a hurricane, tornado, Flooding, a successful ransomware attack, supply chain disruption, or extended power outage, businesses need to be prepared to ensure continuous operations even when disaster strikes.
Let's Get
Started
We help keep your company, end users and data protected.
Connect with us to learn more about how we can help you modernize, optimize, stabilize and secure your technology investments.
